As video conferencing continues to grow in importance for businesses, end-to-end encryption has never been a more critical feature for securing this communication channel. You need to have confidence in your conference call services and overall collaboration solutions. Are they always available? And are they “securely available”? And are your communications themselves available to you and your teams… and no one else?
End-to-end encryption (E2EE) is the next step in secure communications. But what is E2EE, exactly? How does it secure messaging, video, and phone communications? What does it protect against? And who can access these E2EE communications? Let’s find out.
In this article, we’ll cover:
- What is end-to-end encryption?
- How does end-to-end encryption work?
- The top benefits of E2EE for cloud communications
- End-to-end vs point-to-point encryption
- How to choose the right encryption for your business communications
- Coming soon: E2EE for RingCentral MVP
What is end-to-end encryption (E2EE)?
End-to-end encryption (E2EE) is a powerful security and privacy control that ensures your online meeting contents are confidential and secure. E2EE provides privacy for privileged conversations as well as security protection against third-party intrusion and cyber attacks.
How does end-to-end encryption work?
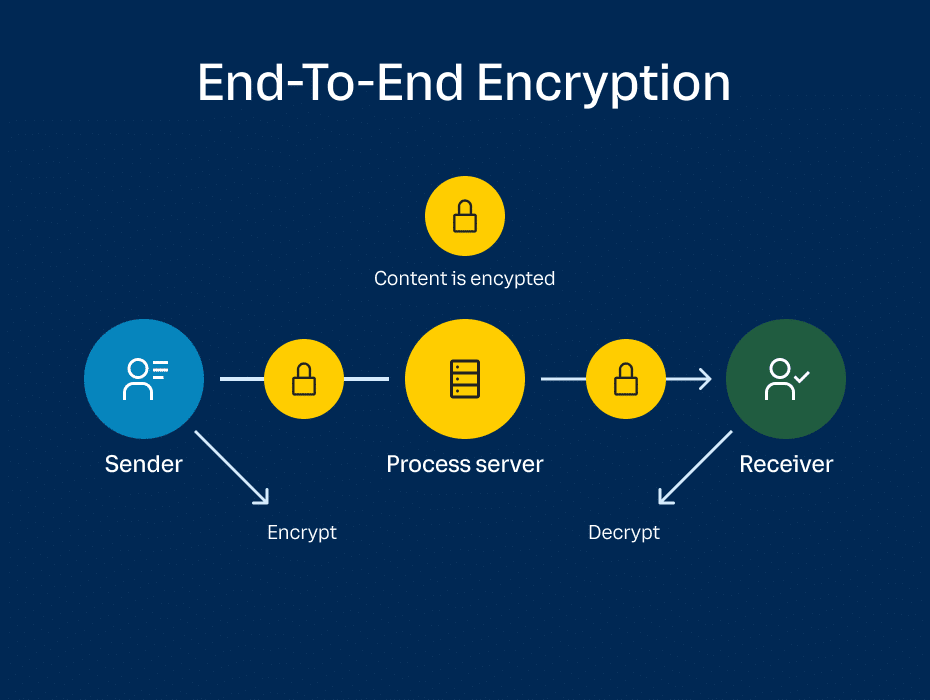
End-to-end encryption (E2EE) technology prevents any unauthorized third party from accessing users’ communications, whether it’s video conferencing on a VoIP phone, chatting via an instant messaging service, or anything else. With E2EE, the endpoints (sender and receiver) are able to establish encryption keys without the involvement of any intermediaries. The endpoints can then use these keys to encrypt (and decrypt) data, as seen in this diagram:
2 major benefits of E2EE for cloud communications
For video meetings where you want total privacy and data security, E2EE adds an extra layer to mitigate risk and shield sensitive information.
As a result, there are two really important benefits that E2EE provides for video conferencing:
1. Confidentiality (Protection against eavesdropping)
With E2EE, data is encrypted the entire time it traverses the provider’s network. Because only participants can decrypt the communications, bad actors at the provider’s side—or anywhere in between—can’t eavesdrop on your communications.
2. Integrity (Protection against modification)
With E2EE, if someone tries to modify or tamper with your communications, you will know because they won’t decrypt properly.
End-to-end vs point-to-point encryption (P2P)
Encryption of data in transit, over public and private networks, uses industry standard protocols to set up encrypted channels to protect data in transit between two points (known as point-to-point (P2P) encryption).
When used with standard protocols such as TLS, SRTP, even HTTP/S, P2P encrypted channels are established between two systems, such as the application used by the video participants and the video provider’s processing systems.

Point-to-point data-in-transit encryption:
- The sender’s channel encrypts data to send to the provider (the video provider).
- The receiver‘s channel decrypts data received from the sender.
- The receiver (video provider) processes (unencrypted) information.
- The receiver’s channel encrypts data to send to the sender.
- The sender’s channel decrypts data received from the receiver (the video provider).
End-to-end encryption:
- The sender’s channel encrypts data to send to other participants via the video provider.
- The video provider processes encrypted information.
- Other participant‘s channels decrypts data received from the sender.
P2P solutions result in the video conferencing provider setting up a P2P channel with each video conference participant. If there are 17 participants, the video conference provider has 17 P2P channels to manage with full access to all communications across these 17 channels.
This allows the video provider to provide additional features, such as virtual backgrounds, meeting transcription and closed captioning, and chat translation of the decrypted ”in the clear” communications.
E2EE is different from standard encryption. With standard encryption, which is on by default, data in transit is encrypted using Transport Layer Security (TLS), and data at rest is encrypted with AES-256. Additionally, with standard encryption, RingCentral is able to provide additional benefits to enhance the communications to make a richer user experience – such as recordings, AI transcripts, whiteboards, and much more.
With E2EE enabled, RingCentral cannot offer these enhanced experiences but in exchange provides the utmost privacy and security for an organization’s communications.
How to choose the right encryption for your business communications
Remember that there are advantages and disadvantages to both end-to-end (E2EE) and point-to-point (P2P) encryption.
With E2EE, you have total confidentiality and peace of mind that your video meeting is fully private—but value-added services such as live transcripts and cloud recording won’t be available.
With P2P or encrypted data-in-transit, you have protection from eavesdroppers while your communications are en route from sender to receiver; explicit provider access allows value-added services including live transcripts/closed captioning, cloud recording, and more. If you need to uplift your security, then E2EE is the way to go.

Of course, how you approach each video meeting will be different. For example, a monthly all-hands meeting might benefit from services like closed captioning. A meeting to discuss sensitive financial or legal information, however, requires total privacy and deserves the uplifted security of end-to-end encryption.
When coupled with RingCentral’s high availability (99.999% uptime, or less than 5 minutes of unplanned downtime a year), RingCentral’s E2EE video conferences provide unparalleled security and data protection with confidentiality, integrity, and availability.
Coming soon: End-to-end encryption for all of RingCentral MVP
In 2021, RingCentral launched end-to-end encryption for our video conferencing. Now, we’re expanding E2EE to our business phone and team messaging solutions.
Today, we’re announcing end-to-end encryption for phone and messaging (E2EE) will be available in a closed beta for select customers in its flagship RingCentral MVP® product in December 2022. RingCentral’s E2EE provides security and privacy for privileged conversations and protection against 3rd-party intrusion and attacks.
E2EE removes the need for multiple encryption products, modernizes the user experience and reduces privacy concerns within privileged conversations.
Best-in-class, end-to-end encryption
- Coming soon for phone and messaging (E2EE for video launched in 2021)
- Goes beyond 1:1 calls and chats and supports large groups
- Available on multiple modalities – desktop app, mobile app and web browser
- Available whether the conversation is ongoing, scheduled, or spontaneous
With E2EE, no unauthorized 3rd party can access communication content: including RingCentral. Think of us as the conduit between two or more parties but the communication content travels through RingCentral. We cannot read, see or hear what’s being communicated.
This functionality will be available to all RingCentral MVP users—whether they are inside a company communicating with each other or interacting with external guests—as long as they are signed into a RingCentral account.

End-to-end encryption for RingCentral Phone
Functionality available (closed beta starting December 2022):
- Turn on/off at the organizational level
- Available for 1:1 calls, supports large groups in H1 2023
- Supports soft phones (desktop and mobile app)
- Ability to convert non-E2EE calls to E2EE
- Ability to convert E2EE calls to E2EE video meeting
Functionality unavailable:
- Call recordings
- Guests (not signed into a RingCentral account)
- Callers from PSTNs
- Callers from hard phones
End-to-end encryption for RingCentral Messaging
Functionality available (closed beta starting December 2022):
- Turn on/off at the organizational level
- Ability for IT admins to manage within the RingCentral desktop app
- Supports soft phones (desktop and mobile app)
- Create team chats for up to 50 participants

Functionality unavailable:
- Sending GIFs
- Creating tasks, events, notes
- Code snippets
- Third-party apps
- Guests (external users / email addresses) cannot join E2EE team chats
- Sharing team disabled
- Notification previews
Key management

With E2EE cryptography, the private keys are stored on the endpoint devices and E2EE messages can only be decrypted using these keys.
Let’s use an example of video or voice. A RingCentral user generates audio or video streams that are encrypted, packetized, and then sent to the backend RingCentral servers. The backend then sends it further to the recipients. But only the recipients can decrypt it.
The key management is completely outside of the backend even though it distributed them. The backend works directly with the endpoints for key distribution.
Scalability through Message Layer Security (MLS)
We built our E2EE using Message Layer Security (MLS). MLS is a security layer for encrypting messages in groups of size two to many. It is designed to be efficient, practical and secure. In contrast, other popular consumer and business applications that utilize E2EE technology use the Signal protocol, which is a non-federated cryptographic protocol that can be used to provide end-to-end encryption for any virtual call or instant messaging conversation.
However, Signal-built E2EE solutions are not as scalable when compared to MLS-built ones. As a result, they will have performance issues such as CPU usage, memory issues and lag when going beyond 1:1 conversations – a limitation that does not exist with RingCentral E2EE as a result of using MLS.
Privacy by design
For compliance minded organizations, IT administrators can turn E2EE on/off at any time. Additionally, IT administrators have cryptographic access to messaging data and can export messaging data if needed. RingCentral also plans to empower customers to enable content capture and supervision with select partners for E2EE voice, chat, and video next year.
Our vision for enterprise-grade E2EE
“With RingCentral’s E2EE for video, and soon, phone calls and messaging, organizations can leverage RingCentral’s native capabilities to simplify their technology stack with one offering. We believe our approach to end-to-end encryption across message, video, and phone is truly differentiated, and represents the most complete deployment of E2EE for enterprise communications, to date,” said Michael Armer, chief information security officer at RingCentral.
“People exchange millions of calls and messages a day on RingCentral’s platform. With our new E2EE, we’re extending enterprise-grade privacy and security controls for our customers, giving them the freedom to have confidential conversations across any mode.”
Updated Aug 19, 2024