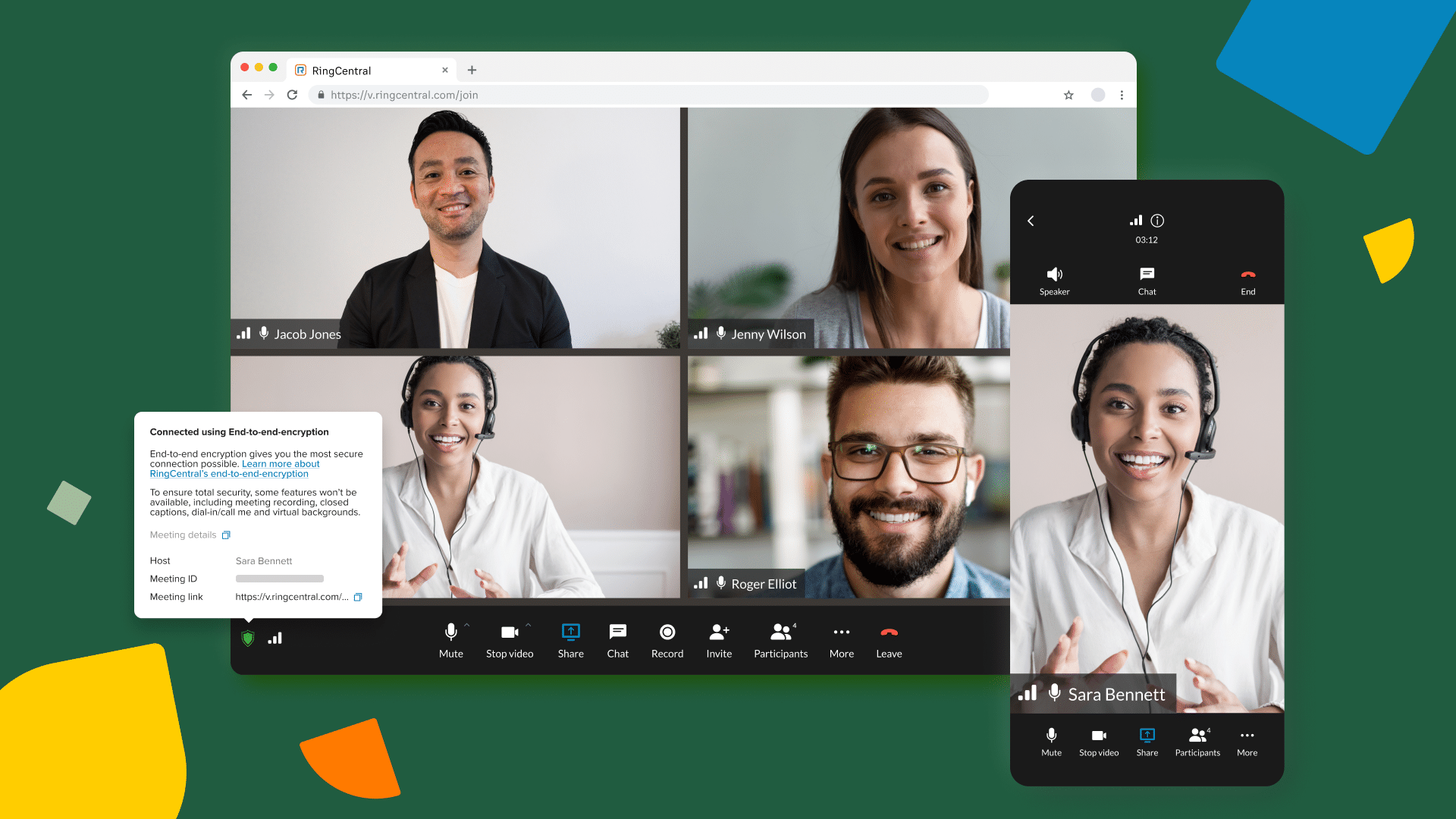
Many companies use hybrid and remote work arrangements—so a video call or phone call online is a crucial part of business.
That means it’s vital that you properly protect your video meetings, so no unwanted viewers can access your private information. To do this, you need to use end-to-end encryption.
What is end-to-end encryption?
So, what does end-to-end encryption mean? In the context of video meetings, end-to-end encryption (E2EE) means video conversations are kept exclusively private to participants.
With end-to-end encryption, all video content is encrypted as a conversation starts, and decrypted—turned back into normal video form—only for those with access. For everyone else, end-to-end encryption means that the video information is impossible to access
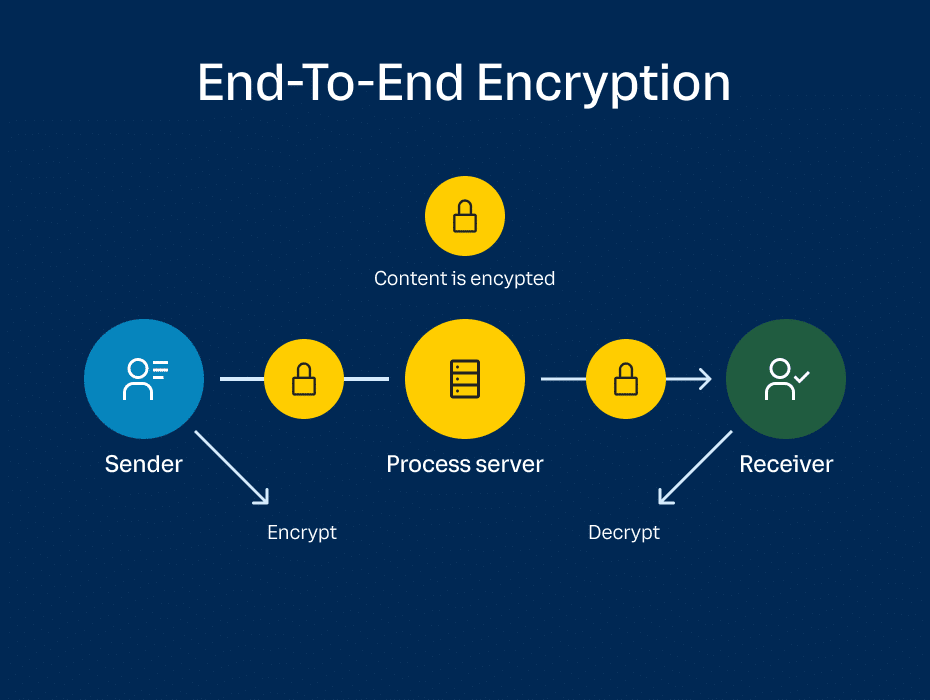
So how does E2EE compare to the older point-to-point (P2P) encryption? P2P encryption covers endpoints, proxies, and process servers, using protocols such as Transport Layer Security (TLS) and SRTP (Secure Real-Time Transport Protocol) to protect video meeting data between all points.
P2P encryption allows providers to provide advanced video meeting features like closed captioning through secure access to backend audio content.
End-to-end encryption (E2EE) goes beyond P2P video meeting encryption by adding an extra layer of security.
The extra layer in your VoIP phone service means you don’t have to worry about eavesdropping or interference from your provider, and can rest assured your video meetings will remain strictly confidential.
Why is end-to-end encryption important?
End-to-end encryption is crucially important for numerous reasons. As mentioned, it keeps your data secure whenever it’s sent between users. So, encrypted data is virtually invulnerable to unwanted access.
This means that you don’t have to worry about your data even when it’s sent through unsecured or compromised networks. With end-to-end encryption, you can also rest assured that your data won’t be tampered with or modified when sent between users.
And, by using end-to-end encryption, you signal your commitment to the highest security standards. The highest-level handlers of sensitive information, such as the U.S. Department of Defense, use end-to-end encryption. They do this to comply with regulations such as ITAR (International Traffic in Arms Relations) and CMMC (Cybersecurity Maturity Model Certification).
What is dynamic end-to-end encryption?
Dynamic end-to-end encryption (D-E2EE) adds yet another layer of security to your video meetings, and gives you the ability to turn end-to-end encryption on or off at any point during a meeting.
For example, you can turn on D-E2EE in the middle of a meeting to discuss particularly confidential information, and turn it off again when that discussion has ended. This reassures everyone in the meeting that only internal participants can access the information.
Here are some examples of when you might want to switch to E2EE during a video meeting:
- A general HR meeting that unexpectedly turns into a discussion about your employee payroll and individual compensation
- A C-Suite discussion that spontaneously shifts to a conversation about future earnings and acquisitions
- A conversation about healthcare that abruptly changes due to an emergency
Whether a sensitive conversation is spontaneous or planned, being able to toggle between E2EE and D-E2EE means you can choose how you approach your privacy.
Why RingCentral’s dynamic end-to-end encryption is different
So, end-to-end encryption is a must if you want to keep your data safe—and RingCentral dynamic end-to-end encryption goes even further.
RingCentral dynamic end-to-end encryption offers you maximum data safety. We use the best internal security protocols to give your users complete privacy when they need it, and we give you everything you need to keep your information safe.
Dynamic end-to-end encryption will suit your team, wherever you are, however you work. Here’s what D-E2EE offers.
1. You can use D-E2EE on every app
You can use our dynamic end-to-end encryption on the RingCentral desktop app, mobile app, and on browsers (Google Chrome and Microsoft Edge).
2. You can use D-E2EE on any device
Our dynamic end-to-end encryption is available for your PC, phone, or tablet.
3. You can use D-E2EE in any kind of meeting
You can use our dynamic end-to-end encryption for one-to-one meetings, large conferences, and everything in between.
How to turn on end-to-end encryption in RingCentral Video
You turn on D-E2EE in the same way on every RingCentral app (desktop, mobile, browser):
- Select the ‘“More’” icon on the bottom left of the meeting panel.
- Select the ‘“Turn on End-to-End Encryption’” button in the menu.
- Select ‘“Turn it on’” in the pop-up modal to confirm.
Once you’ve activated D-E2EE, you’ll see a green shield in the bottom left corner of the meeting panel. When that icon appears, this means everyone in your video—and everything they say—is protected by the highest level of encryption.
D-E2EE does limit some advanced capabilities, as it restricts RingCentral’s ability to access data. The following capabilities aren’t available when you use D-E2EE:
- Recordings
- Transcripts
- Extra participants joining by phone (they will have to re-join after authenticating with the RingCentral app)
- Closed captions
-
Dynamic end-to-end encryption: Complete privacy when you need it
If you use sensitive data, you need end-to-end encryption. And if you want the best possible safeguard against data theft or interference, RingCentral dynamic end-to-end encryption is the indispensable security measure you need.
If you already use RingCentral RingEx, you can already benefit from dynamic end-to-end encryption. If you haven’t tried RingCentral RingEx yet, why not request a demo today?
End-to-end encryption FAQs
What does end-to-end encryption mean?
People often struggle to fathom a workable end-to-end encryption meaning. End-to-end encryption means data is turned into an unreadable form between two specific points to keep it private.
Only those with the required encryption keys are permitted to decrypt (translate back into its original form) and read the end-to-end encrypted data.
What is ciphertext?
Ciphertext is unreadable encrypted data. An encryption algorithm changes readable data into ciphertext, which can only be retranslated by someone in possession of a unique decryption key. Without the decryption key, anyone who tries to intercept an encrypted message can only see ciphertext—an unreadable string of letters, numbers, and symbols.
What is encrypted when you use end-to-end encryption?
When you send an end-to-end encrypted message, the full message is end-to-end encrypted, whenever a public encryption key is available for the recipient.
What are encryption keys?
An encryption key is a random string of bits used by an encryption algorithm to turn readable data into ciphertext.
Some types of encryption use the same encryption key to encrypt and decrypt data (symmetric encryption), while others will use different encryption and decryption keys (this is asymmetric encryption). The most common type of encryption methodology is a combination of the two types—hybrid encryption.
What is PGP?
PGP is the most widely used email encryption system, and stands for Pretty Good Privacy. PGP encryption transforms your messages into unreadable ciphertext before they are sent over the internet to a recipient.
PGP also verifies that the message was kept intact while it was sent. If encryption keys are obtained from a trustworthy sender, it also authenticates their identity.
Updated Aug 22, 2024