BYOD (bring your own device) isn’t a new concept, but its popularity has soared recently—so much so, that the market is predicted to exceed $430 billion by 2025.1
It’s clear that employees want to work anytime and anywhere (and from any type of device), and just as importantly, companies are happy for them to do so.
The rise in BYOD is mainly due to the rise in the number of smartphones and mobile devices we’re all using, as well as the increasing numbers of businesses allowing their employees to work from anywhere. The uptake of high speed broadband has also helped fuel the rise of BYOD in both developing and developed countries.
And as the BYOD trend grows, businesses are also starting to realize the importance of putting formal policies and security measures in place. Whether it’s just you and two other employees in a small business, or you’re starting to build out more teams or departments, having a BYOD policy is useful—especially with the lines blurring between employees using their devices for not only work, but social media and personal use as well.
Keep reading to learn:
- What is BYOD? A quick background check
- What exactly is a BYOD policy?
- What should a BYOD policy include?
- Is BYOD really a good idea?
- What are the risks of BYOD?
- How to create a good BYOD policy in 8 steps
- How having the right tools is essential to successfully implementing BYOD
👀 Grab the free Work-from-Home (-or-Anywhere) Policy template!
What is BYOD?
BYOD refers to the practice of “bringing your own device” into the workplace.
The trend started when employees began bringing their own smartphones and other personal devices into the office. Seeing that personal devices were often more technically advanced than work devices, companies and IT departments started to allow employees to use them to perform work-related tasks.
What exactly is a BYOD policy?
A bring-your-own-device policy is essentially a set of guidelines that allows employees to use their personal devices, like smartphones, tablets, and laptops, to access company networks or systems.
BYOD policies help make sure employees are securely connected to, say, their work email inboxes—with the convenience of being able to work from any location and during more flexible hours.
What should a BYOD policy include?
Of course, it’s always essential to think carefully about your policy before allowing employees to freely use their own devices on your business’ network. But that’s especially true if you work in a more regulated industry like healthcare, finance, or law.
A BYOD program typically includes three critical components:
- A software application for managing devices connected to a network
- A written policy outlining the responsibilities of employers/users
- An agreement that employees must sign to acknowledge they’ve read and understood the policy
To help you create a policy, there are actually many useful templates available that can be adapted to suit each company’s requirements.
A sample BYOD policy template:
A “bring your own device” policy should include items like:
- Terms of acceptable use: Include activities that directly or indirectly support the business, as well as reasonable personal use time.
- Devices and support should be listed: For example, iPhone and Android/Windows phones along with details of models and operating systems.
- Reimbursement: Include whether the company is paying an allowance to cover either the entire phone plan or half, etc.
- Security concerns should be clearly identified including use of passwords, PINs, failed login attempts, loss of device, viruses, or policy breaches. You can access a password policy template here.2
- Risks and liabilities including ethical considerations and liability for risks (e.g., loss of data due to downloading viruses or crashes) should be outlined here as well.
Is BYOD really a good idea?
In most cases, yes!
BYOD can be a very good idea—for businesses of all sizes—for a few reasons:
- Bringing your own device can help make your team more productive and mobile. And since people tend to be more familiar with their own devices and apps, this could help them execute tasks more quickly—and without needing as much technical support.
- In fact, studies have shown that allowing staff to work using their own devices could improve productivity by up to 34%.3
- The key component of adopting a BYOD policy is that employees can work remotely or bring their own devices to the office to do work-related tasks. This eliminates the need for companies to buy additional hardware and is can be a big cost saving.
- A successful BYOD policy has the advantage that workers can do their jobs according to the schedule that works best—for both themselves and the customer or client.
See how CFM Insurance implemented a BYOD policy successfully to keep service its policyholders—from anywhere.
Bonus: A bringing your own device policy can help you get 5G-ready
BYOD may also help businesses get 5G-ready—without the added legwork. Demand for 5G is gaining momentum, and if your employees are up on the latest devices, chances are theirs are already 5G-enabled. This means that BYOD could lessen the financial burden of your company having to provide the latest tech for each device holder.
What are the risks of BYOD?
As with most things in life, there are pros and cons of implementing a BYOD policy.
| Pros | Cons |
| Cost-savings—less investment needed in hardware | IT support team has to deal with a broader ecosystem of devices |
| Employees are already familiar with their own devices | Potential device security risks, especially with sensitive information |
| Personal devices are often more up-to-date | Fears of lost employee privacy if companies can access personal data |
| Higher employee morale | Exclusion of workers who don’t have the latest devices |
When employees use their own devices, there’s always the potential for creating a security risk, particularly when they’re accessing sensitive work-related networks.
And beyond network security, the line between personal and work-related data could, in theory, blur. Workers might (very understandably) fear that their employers can access the information stored on their personal devices, like their social media accounts and contacts.
The solution: Good mobile device management (MDM) will mitigate the risks
These problems can also be overcome by making sure that you have rules around managing data within your BYOD policy. This should address your customer or client data, your company data, and of course, the employees’ own personal data on the devices.
How to create a good BYOD policy in 8 steps
To really reap the benefits of BYOD, you need to have a thoughtful and deliberate approach. (Don’t rush this.) Companies need to manage personal devices without hindering privacy or security and without putting a strain on cost-management. Here are 8 key steps to getting your BYOD policy right:
1. Decide whether BYOD is right for your business. The first and most important step. For most businesses, BYOD is fine, but for certain folks, BYOD just isn’t a good idea. Financial advisors working for super-elite billionaire clients, for instance, may want to stay away from BYOD.
2. Create your IT policies on paper before getting into the specifics of a BYOD system. Consider your goals (whether it’s to minimize customer service downtime or increase productivity) and craft an acceptable use policy that defines best practices and governance.
3. Decide the scope of acceptable devices. For example, Android smartphones, specific iPhones, or all iOS devices? Find out which devices most employees own and which ones can you effectively monitor using your BYOD management system. Consider whether you want them to access company Wi-Fi or use their own data plans.
4. Keep personal information and company data separate. If you don’t get this right, you’re putting your business at significant risk of a data breach. Take a multi-faceted approach. Require the team to use specialized apps (ideally with 2-factor authentication), especially when it comes to storing company data. (Remember, these requirements can be part of your BYOD policy.)
Choose apps that can be deleted remotely in the event the device is lost or an employee leaves.
5. Offer training on cybersecurity—and make it clear employees have a role in managing security. Implement a strong security policy and educate everyone on the need for strong passwords, malware threats, and other risks.
6. Plan how you’re going to protect private data by evaluating your apps and BYOD policies for privacy protection. For example, your device management software should never copy, store, or even interact with an employee’s data.
7. Make the signup process for BYOD simple and use ticket systems to track requests. Set-up should be simple, too, so your employees can get started ASAP.
8. Regularly review everything from data usage to policy compliance. Things change fast, especially when it comes to technology and security. Make sure that you’re reviewing your BYOD policy and what the tech landscape looks like at least once a year to make sure you’re not falling behind!
And now, a few other tips…
Use a cloud-based communication platform
Instead of getting your team to use a smattering of different apps to stay in touch (one for video conferencing, one for messaging, and so on…), why not streamline the number of tools you’re using?
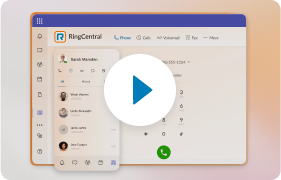
A cloud-based communications system gives you access to a variety of communication channels in one simple platform. For instance, RingCentral’s desktop and mobile app gives you team messaging, video conferencing, and a phone service—all in one handy app:
When everyone is bringing their own devices, it’s easy for everyone to be using their own apps or whatever they’re used to. And for company communications, the big benefit of having one all-in-one platform is that if they’re not already using the app, they only have one thing to download.
RingCentral also integrates with other popular cloud applications too, letting you work together with your team more efficiently. The flexibility of cloud-based collaboration lets everyone connect to the company network and do their jobs—no matter where they are.
Determine how you’ll secure personal devices and maintain a consistent brand
Your cell phone, when used with a cloud-based phone calling app, should give you the ability to show a business phone number when you’re calling clients, partners, and anyone else for work. This allows you to maintain your company brand (and your own privacy) when you’re using your own phone on the go.
For example, the RingCentral desktop and mobile app lets you make and receive calls on your own mobile device while showing your business number and shielding your personal number. This means you only have to have one device with you at any one time, which makes life much more convenient:

In fact, MHP&S, a law firm based in Tennessee, did exactly that: their lawyers can take calls from clients even when they’re out of the office—and their clients are none the wiser!
🕹️ Get a hands-on look at how RingCentral works by booking a product tour:
💰 You can also use this calculator to see roughly how much your business could save by using RingCentral to support your team’s communication with each other—and clients.
Always follow BYOD best practices
Best practices are there for a reason. And if you can follow BYOD best practices whenever you can, you greatly increase the chances that you’ll be successful. For example, skipping straight to policy creation before getting both stakeholder agreement and employee buy-in is a common mistake. (It’s essential, too, to make sure that your IT and security team are already in the loop before policy development takes place.)
Make sure you collect the views of all the different proposed user groups across all job sectors before settling on a course of action. Then, the policy needs to be looked over by the legal team before being enforced. It must cover thorny issues such as stolen devices or charges over and above a normal data plan, after all.
Building policies solely on the company’s interests is a bad idea. As is implementing policies that are too restrictive or fail to offer support for the right devices. This will disengage employees and waste valuable time and money. Getting input from human resources may help here.
Having the right tools is essential to successfully implementing a BYOD policy—are you ready?
Again, BYOD policies can work well for both big and small companies in different industries. But it’s still important to assess the impact this will have on privacy, company data security, and IT support. Think about the types of devices your employees want to use for work and consider how to handle devices when employees leave the company.
Most importantly of all, when you’re implementing a BYOD policy, make sure you use the right tools. (For instance, choose tools that let you make and receive calls on a personal smartphone but show the business number instead of your personal number.)
BYOD is a major opportunity for companies of all kinds—yes, even small businesses—to become way more agile and flexible in the way they work, and even save money too. But both the system and policy need to be worked out in detail (and in collaboration with your IT person, if you have one) before introducing a BYOD way of working.
When implementing a BYOD policy make sure you consider the types and number of devices you’ll need to manage. Take the time to identify the right tools to keep you connected and secure, whether staff are in-house or working remotely, and you’ll be on the right path to start bringing your own devices to work!
1 mordorintelligence.com/industry-reports/byod-market
2 itmanagerdaily.com/password-policy-template
3 cassinfo.com/telecom-expense-management-blog/the-future-of-byod-6-key-trends-for-2020
Updated Mar 13, 2025